BLOG
How to Ensure Software Supply Chain Security with Signed Releases
Connected devices are an integral part of our daily lives. From smartphones and self-driving cars to streaming services and mobile banking, the world seemingly runs on software.
But a world run on software is one that’s susceptible to malicious cyber attacks. Vulnerabilities to any component of the software supply chain provide hackers with the opportunity to insert malicious code into systems, compromising the security of intelligent infrastructure, including the power grid, transportation agents, and communications services.
As a result, any company that develops and releases software should take software supply chain security seriously. In this article, we’ll dive into one of the key components companies should implement to keep their supply chain safe: signed software releases.
Software Supply Chain Security 101: Generate Signed Releases Using Public Key Infrastructure
Releasing signed code is key to preventing your software from being vulnerable to malicious attacks.
Signed releases use what are known as cryptographic signatures to establish trust in the software supply chain. These signatures help identify users and digital information by creating a virtual fingerprint unique to a specific person or entity. Cryptographic signatures employ asymmetric cryptography, which involves a pair of keys: a private key for signing and a corresponding public key for signature verification. Public key infrastructure (PKI) is vital in managing these key pairs, certificate issuance, and certificate revocation.
To sign a software release, the software publisher must generate a cryptographic hash of the release artifact, such as a binary file or a source code archive. The publisher then encrypts this hash using their private key, creating the digital signature. This signature is either embedded in the software or distributed separately.
Recipients of the release can verify the signature by decrypting it with the corresponding public key, obtaining the original hash. Then, they can independently compute the hash of the software they received and compare it to the decrypted hash. If the hashes match, the signature is considered valid, and the release is deemed authentic and unaltered.
How Signed Releases Benefit Software Supply Chain Security
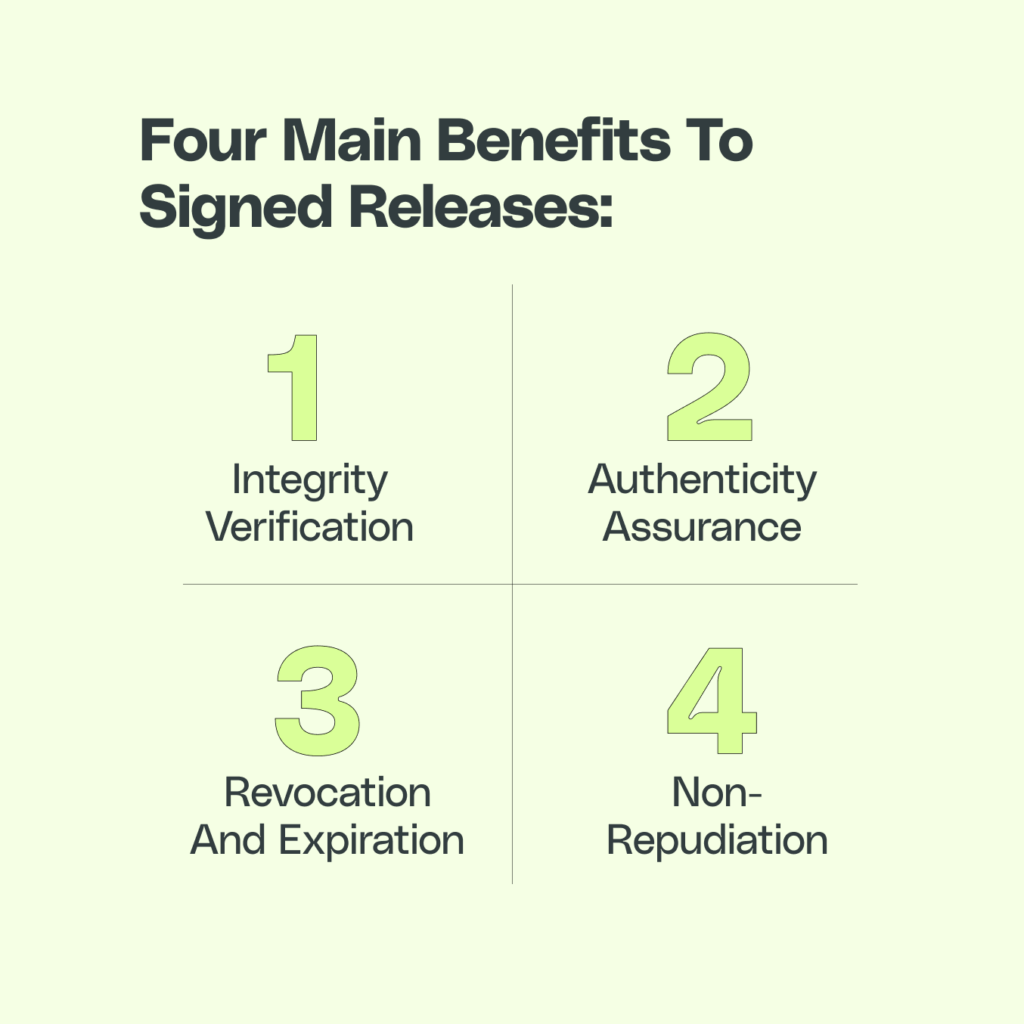
Signed releases enhance software security by providing a verifiable digital signature, generated by the software publisher’s private key, to ensure the integrity and authenticity of the software. There are four main benefits to signed releases:
- Integrity Verification: Signed releases provide a mechanism to ensure that the software artifacts have not been tampered with during transit, distribution, or storage. Any unauthorized modification of the file will result in a mismatch of the computed and decrypted hashes, alerting the recipient to potential tampering.
- Authenticity Assurance: Cryptographic signatures confirm that the software release originates from a trusted source. By verifying the signature, recipients can ensure that the release was signed by the holder of the private key, which is ideally a known and reputable software publisher.
- Non-repudiation: Digital signatures provide non-repudiation, meaning that the signer cannot deny having signed the release. This feature ensures accountability in the software supply chain, as publishers can be held responsible for the security and quality of their releases.
- Revocation and Expiration: PKI enables the management of certificate revocation and expiration, allowing for the revocation of compromised keys or the phasing out of outdated cryptographic algorithms.
Best Practices for Implementing Signed Releases
Below are four best practices to keep in mind while implementing signed releases into your software supply chain.
- Key Management: Protect private keys with strong encryption and securely store them in hardware security modules (HSMs) or other trusted environments. Establish procedures for key rotation and revocation to mitigate the risks associated with key compromise or algorithm obsolescence.
- Certificate Authority Selection: Choose a reputable and reliable certificate authority (CA) to issue certificates for your public keys. The CA should follow strict security standards and offer transparency in their practices to establish trust in the signed releases.
- Release Pipeline Integration: Incorporate the signing process into your release pipeline, ensuring that every artifact produced is signed with the appropriate private key. Automate the signing process to minimize the risk of human error and ensure consistency across releases.
- Signature Verification Enforcement: Implement strict enforcement of signature verification in your software distribution systems, rejecting any release that fails the verification process. This measure ensures that only authentic and unaltered releases are distributed and installed.
Final Thoughts
Signed releases play a crucial role in ensuring software supply chain security and accountability by providing integrity verification, authenticity assurance, and non-repudiation. Implementing a robust PKI-based signing process, coupled with diligent key management and release pipeline integration, significantly enhances trust and security in the software supply chain.